Facebook has recently published a technical paper regarding a threat actor named APT-C-23.
Almost half of their report is about a new iOS malware that is in use by the threat actor.
Facebook called this malware Phenakite and provided 2 hashes of malware samples, however, those samples are not publicly available (yet).
Since I am Android type of person, naturally the Android malware interested me more than the iOS malware.
After playing a little with the Android malware, I decided to see what I can learn about the iOS malware, but how? I don't have any sample and I am quite clueless with Apple devices at every possible level. Well:
We don’t need bombs we got fire kites
Fortunately, the distribution site of the malware was still alive:
Well, not much to do other than download the app, well the link is not directly the app apparently:
But now what?
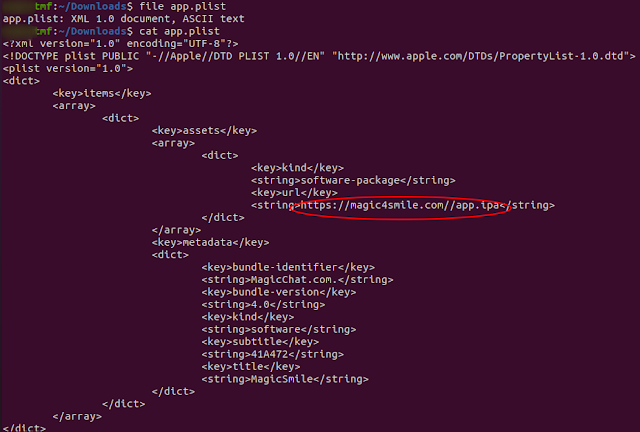
Feeling stuck? no worries I felt the same as well. Since I don't have iOS device to try it out, I decided to inspect the code of the website:There was also a reference to a file named app.plist lets try to grab it, shall we?
Ok, this is plain text and simple, the software package is app.ipa, lets grab that as well:
Ah, close, but no cigar, this hash doesn't match the two samples in Facebook report.
Could it be a new sample? doubt it, look at the date. So what is this file? ipa obviously! Not to be confused with IPA.
Essentially it is a Zip file, so lets unzip that payload:
Congratulations, this is the first time the blog actually does what it stands for, sharing malware for everyone with a hint of analysis. (if you are reading this too late and the distribution site of the malware is down, no worries, it is also available at VirusTotal as a standalone and as an archive)
Now you can enjoy your own copy of Phenakite and start reversing the Mach-O if you know how to :)
Bonus lol's:
The terms of service of the malware is.... Lorem Ipsum :
The privacy is seem to be borrowed from "relatedcode.com" which has an open source chat for iOS repository, this is most likely the chat app that Facebook was referring to:
All your base is on fire:
More interesting strings:
app











No comments:
Post a Comment